One of the most frustrating problems I have dealt with recently is maintaining system controls with the variety of people and passwords and networks and logon's including applications and client servers that control our systems for protecting us.
In general I have always used a series passwords that are and remain the same. However there are changes being made that have increased my list of those passwords to an unmanageable point. Now enter case sensitivity and numerical mandatory combination expressions and I am in trouble if I make a mistake with a cap letter or a &^$#^$#*^ instead a number. Here are some pointers I have stumbled upon for cleaning up this mess once you have made the mistake on the computer YOU own and have LOCKED yourself out. Remember - YOU are not the enemy and you have absolute control of this machine!
Sheepy
Beginners Guides: Forgotten Passwords & Recovery Methods
Ever wondered how to recover or reset a forgotten password in WindowsXP? This guide will help you get back into your computer, all without reinstalling the operating system. - Version 1.1.0
Windows 2000 and XP brought with them enhanced security features designed originally for the business environment. Unlike the Windows 9x/ME series of operating systems, these new operating systems have very effective password security measures which you can use to protect your system and your data from unwanted access.
Of course, what happens if when you forget the passwords? Congratulations… You've just become "the enemy" as far as your computer is concerned.
Fortunately, for every method of password protecting a computer system, there is a method of defeating said protection, especially if you have physical access to the computer. Since it's your PC, that shouldn't be a problem, so cheer up.
In this guide, PCstats will explore the various methods that can be used to password protect computer systems, and how to defeat them if you lock yourself out. We'll start with non-user account related passwords, like the computer BIOS password and Internet Explorer passwords, and proceed on to methods of breaking into your system again if you manage to completely lock yourself out.
How to get around BIOS passwords
BIOS passwords are one of the oldest methods of protecting computer systems from unauthorized use, and also one of the least used. Why? Well, password protecting your computer BIOS is a simple and effective means of locking unwanted intruders out of your computer, provided they have no access to the box itself or no hardware knowledge. If they do, it's the equivalent of locking your house and leaving your back window open. Fortunately for you, if you forgot your keys inside, it's easy to get back in.
All motherboards have a stored default configuration for their BIOS, which does not include password protection, for obvious reasons. Therefore, to defeat a BIOS password, all you need to do is manually reset the motherboard BIOS to its default settings. Please note that resetting the BIOS to remove a password will also remove any other changes you have made to the default settings. Resetting the BIOS can be accomplished in one of two ways.
 Most modern motherboards have a jumper built onto the board which will clear the CMOS (the onboard memory which stores any changes made to the default BIOS settings). Clearing the CMOS removes any changes made to the default BIOS settings. Generally this jumper is located next to the motherboard battery itself, but we recommend that you consult your motherboard manual for the correct location.
Most modern motherboards have a jumper built onto the board which will clear the CMOS (the onboard memory which stores any changes made to the default BIOS settings). Clearing the CMOS removes any changes made to the default BIOS settings. Generally this jumper is located next to the motherboard battery itself, but we recommend that you consult your motherboard manual for the correct location.
Note that some boards do not have a jumper in this position, but rather two contacts which you will need to (carefully) bridge with a metal object like a screwdriver.
To clear the CMOS using the jumper: Turn the computer off, and set the jumper to the closed position (with the jumper bridging both metal pins). Press the power button to turn the computer on. Your system will not power up, but the CMOS is cleared by this action. Then, open the jumper (put the jumper back to the default position) and power on the computer normally.
You will most likely be stopped in the POST screen and prompted to press F1 or another key to set BIOS defaults. Do so, and from the BIOS screen, simply save and exit to load your computer normally, minus the BIOS password.
Resetting BIOS PasswordsIf you are not sure of the location of the clear CMOS jumper, or your system does not have one, there's another easy (but slower) way to clear the CMOS memory and reset the BIOS. Every motherboard has a battery built in which provides the trickle of power the CMOS memory needs to store its information. If you remove the battery for a brief period, the CMOS should lose its stored data.
In all modern motherboards, the battery is a standard CR 2032 Lithium Cell, which looks like this:
To clear the CMOS memory, power down you system and remove this battery (you will probably need a flathead screwdriver to do it) for 5-10 minutes, then pop it back in and turn your system on. You will be prompted to set the BIOS defaults. From the BIOS screen, save and exit, and the password should no longer be set.
While this works well with desktop PCs, notebooks and laptops employ slightly different methods of storing the BIOS password. In most cases, like 99% of the time, you will not be able to reset a forgotten BIOS password by this, or any other user accessible method. Since notebooks are easily stolen, manufacturers have evolved their security measures significantly to help you protect your data, and investment. Look for PCstats Guide to preventing data theft from a stolen laptop soon... In the mean time, when it comes to resetting a BIOS-level password on a notebook, usually the only option available is to send the entire notebook back to the manufacturer for support.
Revealing disguised passwords in Windows XP
With the way that Windows handles non-user account passwords - such as dial in passwords for your Internet service provider, email access passwords or website authorization boxes - it can be very easy to forget the original password that you entered in long ago.
If you have set autocomplete to fill in your password entries in Internet Explorer, for example, you may have only entered each password once, many months ago, no matter how many times you've used them.
Writing all your passwords down for safekeeping is definitely recommended, but how can you when they're all displayed as ***** in Windows?
Well, the solution to this lies in third-party software that can peel back that row of asterisks. There are many freely available software tools for decoding, or revealing passwords in Windows or Internet Explorer dialog boxes.
Using Asterisk-Password Revealing ProgramsThe one we will use for the purpose of this article is called Asterisk Key by Passware. This easy to handle freeware program analyzes covered passwords and reports them to you. To use it, simply open the program, highlight the password box or open the web page containing the covered password and click the 'recover' button.

Of course, commercial software programs are available that can do considerably more than this, for a price. One example of this is Rixler software's Password Recovery Toolbox which scans your system and enumerates all Internet explorer stored passwords, autocomplete data (data you entered repeatedly when filling in web forms), Outlook Express passwords, Internet login passwords, etc.
This information is then presented to you in an easily accessible form. Scary, but very useful for system administrators.
Getting around Windows XP user passwords
Windows XP saves user passwords as an encrypted numerical 'hash' - taking a password of say 'password' and turning it into something like "HT5E-23AE-8F98-NAQ9-83D4-9R89-MU4K." This hash value is then stored in the SAM (Security Accounts Manager) file, found in the C:\windows\system32\config directory.
This portion of the file is then re-encrypted by the syskey utility which considerably strengthens the encryption. The data needed to remove the syskey encryption is stored in the SYSTEM file in the same directory. The directory itself is invisible and inaccessible to all users except the operating system itself while windows is running. By using an alternate operating system that can read your disks, or by transferring your disks to another windows machine, you can gain access to the SAM and SYSTEM files.
Resetting XP user passwords with the Administrator account
All versions of Windows XP include a built in account called 'administrator.' This account has full privileges in XP, and is capable of resetting the passwords for all user accounts. This can be a lifesaver if you have locked yourself out of your normal user account. Use of the Administrator account depends on which version of XP you are currently using.
With XP professional:
You will have been prompted to create a password for the Administrator account during the installation process. If you have this password recorded, or if you entered a blank password (commonly done, but not a secure idea ), then you can access the Administrator account and reset your forgotten password.
To login as administrator: From the Welcome screen, press CTRL+ALT+DEL twice to bring up a login window for the administrator account.
Windows Login PasswordsOnce you are logged in, go to 'start\control panel\user accounts' and change the offending password. Note that if you did enter a blank password for the Administrator account, now is a really good time to change it. While you are at it, change the name of the Administrator account itself to something else, as this is the account that everyone who may try to gain unauthorized access to your system is going to try to crack first.
To do this: Right click on 'my computer,' and select 'manage.'
Expand 'local users and groups' then open the 'users' folder and highlight the 'administrator' account. Right click and select 'rename' to change it.
Windows XP Home does not let you log in with the Administrator account normally. To access it, you must restart the computer in safe mode, a special 'minimal' mode used to correct errors caused by third-party software, among other things.
To enter safe mode: Restart your system. Immediately after the POST screen, press F8 a few times to bring up the XP advanced options menu. Select the 'start Windows XP in safe mode' option.
Once safe mode has loaded, login with the username 'administrator.' The password is blank by default. You can now change user passwords by going to 'start\control panel\user accounts.' Reboot normally when you are done.
Create a Password reset disk:
Windows XP is a fair bit more friendly than previous Microsoft operating systems based off of the Windows NT kernel, at least when it comes to recovering forgotten passwords. Not only can you set a password hint to help you remember a forgotten user password, you can also create a floppy disk which will enable you to completely reset your password in the event that you cannot recall it.
While this will not help you if you are currently locked out of your system, it can certainly put your mind at ease about the possibility of it ever happening again.
Windows XP allows users to create a password reset disk specific to their user account. This disk can be used at the welcome screen to reset your password in the event that you do forget it.
To create the disk: Go to start\control panel\user accounts. Select the account you are currently logged in as. Under the 'related tasks' heading in the top left corner, click 'prevent a forgotten password' to open the forgotten password wizard. Insert a blank floppy disk and follow the instructions to create your password reset disk.
To use the password reset disk in case of emergency: Once you have created a password reset disk for a specific user, the next time the password for that user is entered incorrectly at the welcome screen, a message will pop up asking if you have forgotten your password. At this point you can elect to use your password reset disk. Follow the instructions to reset your login password.
Note: There are is a possible problem with the above procedure if you have used Windows XP's built in encryption feature to encrypt some of your files and folders, but have not yet updated to service pack 1. Do not reset your password in this situation, as you will lose access to the encrypted data. Once you have got service pack 1, it is safe to use the disk.
Keep your reset disk in a safe location, because anyone else can also use it to reset your password.
NT/2000/XP password reset boot utilityThere are utilities available which can directly edit Windows NT\2000\XP user accounts and change or blank their passwords. These generally work by booting the computer into a minimal version of an alternate operating system like Linux, then directly accessing and editing the system32\config files.
An excellent and fairly easy to use example of this can be found here. Files to create a bootable floppy or CD are available from the site, as are instructions. This utility uses a text-only Linux version to allow you to edit user accounts and change passwords. Very effective.
Please note that if you have encrypted files using the built in Windows encrypted file system (EFS), you will lose access to them if you change your password with this program. See the below method for a non-catastrophic alternative.
Extracting a lost password from your hard drive:
If all else fails, but you still have physical access to your computer, all is not lost! You can get hold of the actual file on the hard drive that contains your password information, and use some third-party software to extract the passwords from this file.
As mentioned above, Windows 2000/XP stores its password information in a numerical hash found within the SAM (Security Accounts Manager). The file that contains the SAM cannot be directly accessed by a user (even the administrator) while Windows XP is running. However, if you start your computer with an alternate operating system that has the ability to read the data on your Windows drive, suddenly things become a lot more accessible.
The idea here is to use an alternate operating system (like DOS or Linux) to access the SAM file found in c:\Windows\system32\config and make a copy of it. This file can then be analyzed by one of several password cracking utilities like LC4 or Proactive Windows Security Explorer, which will attempt to obtain the passwords to each user account.
Please not that this procedure is quite a bit more complicated than those in the rest of the article. Unfortunately there is not really an easy way to do this... Please ensure that you read the instructions below very carefully before you attempt the procedure.
We cover three discrete methods of transferring the necessary files to an alternate computer, where you can use a password cracking utility to (hopefully) recover your passwords.
What you will need:
1) Access to another computer. There's no getting around this.
2) At least 2 empty 1.44MB floppy disks.
3) A copy of a command line compression utility like RAR.
4) A DOS boot disk (such as a Windows 98 boot disk which can be obtained from www.bootdisk.com)
Or
4A) Portable Linux distribution like Knoppix.
Or
4B) You will need to transfer the main hard disk (the C:\ drive) from your locked computer physically to your alternate system and install it as a secondary drive, allowing you to copy off the SAM and SYSTEM files easily. For more information on how to do this, see our article on installing a hard disk drive here.
If you use a DOS boot disk and your system drive uses the NTFS file system (the default for Windows XP), you will also need a program that allows DOS to see NTFS formatted drives, such as NTFSDOS. Copy the NTFSDOS executable file onto the boot disk.
5) Password auditing program. For the purpose of this article, we recommend using Proactive Windows Security Explorer, since the beta of this program is freely available, (up to January the 1st, anyhow). LC4, or Lopht Crack4 is better known, but the evaluation version of this now commercial software limits you considerably.
Retrieving the Windows XP SAM and SYSTEM files- With a DOS boot disk -
1. Copy the NTFSDOS file onto your DOS boot disk.
2. Copy the RAR utility files onto one of your empty floppy disks.
3. Boot your system with the boot disk.
If your system drive uses the FAT32 file system :
5. From the a: prompt, insert the disk with the RAR utility.
6. Type: Rar32 a -v a:\systemandsam c:\windows\system32\config\system c:\windows\system32\config\sam
This will copy both the System and SAM files into a compressed file on your floppy called 'systemandsam.' They should all fit onto the one disk, but if not, you will be prompted to insert another blank floppy.
7. Now skip down to the section on extracting passwords.
If your system drive uses the NTFS file system:
8. Type: ntfsdos to detect NTFS formatted drives. The system will inform you which drive letters are allocated to which drives. Make a note of the drive letter of your main drive (the one with windows installed on it).
9. Insert the disk with the RAR utility and type:
10. Rar32 a -v a:\systemandsam (drive letter of your main drive as above):\windows\system32\config\system (drive letter of your main drive as above):\windows\system32\config\sam
11. This will copy both the System and SAM files into a compressed file on your floppy called 'systemandsam.' They should all fit onto the one disk, but if not, you will be prompted to insert another blank floppy.
12. Now skip down to the section on extracting passwords.
- Using a portable Linux CD -
1. These tend to be pretty user friendly, at least compared to most Linux versions… Just boot from the CD.
2. As most current versions of Linux read NTFS drives as well as FAT32, simply navigate to the HDA1\windows\system32\config directory from the desktop and copy the SAM and SYSTEM files to the desktop, then email them to yourself.
From a hard disk you transferred to a new computer
1. Easiest of all. Simply navigate to the (drive letter)\windows\system32\config directory and copy the SAM and SYSTEM files to the location you desire.
Extracting passwords from the SAM fileNow that you have the SAM and SYSTEM files, copy them to your alternate system and start your password auditing software. For the purposes of this article, we are going to describe the process using Proactive Windows Security Explorer.

Select the 'registry files (SAM, SYSTEM)' option and click 'dump.'

Enter the location of the SYSTEM file in the top text box, and then enter the location of the SAM file at the bottom of the screen. Click 'dump'
Brute Force Password CrackingA list of the user accounts found in the SAM file will be displayed. Check the ones you wish to attempt to discover passwords for.
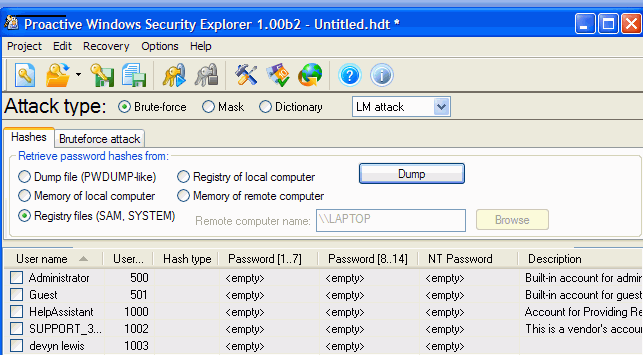
Click the 'brute force attack' tab, then check the 'all digits (0-9)' box unless you are sure the password you need did not contain numbers.
Click the 'start recovery' icon on the toolbar. Please note that cracking the password may take anywhere from 10 minutes to several hours, if it works at all. Complex passwords with different cases and numbers will take much, much longer to crack.
On an other note, if you just want to see how good you own password choices are, you can always follow the steps mentioned above and try to crack your operating system's SAM file as means of conducting your own personal security audit. If you have a Windows password like "cat", chances are it will take only a few moments for the software to discover it. There's also a certain amount of satisfaction from stumping the crack utility altogether, or at least keeping it crunching away for a few days. ;-)
A note on security:
We hope this article has been useful to you. As you can see, there are a fair number of ways to get around Windows 2000/XP's password security systems, especially if you have physical access to the computer in question.
To protect yourself from having the techniques contained in this article used against you maliciously, there are a few basic steps you should take.
Firstly, as we have said in several other articles you must set secure passwords for all user accounts. As you have seen, it is quite simple for password cracking programs to decipher normal dictionary words. Use combinations of numbers and letters, including upper-case letters, to make more secure passwords which will take a discouraging amount of time to crack. In Windows XP, all accounts created during the install process have full administrative privileges, and they do not have passwords by default. Fix this.
Secondly, as you have seen in this article, there is no such thing as a secure password if the potential intruder has physical access to your computer. Keep this in mind, especially if your computers are exposed to the public.
Find out about this and many other reviews by joining the Weekly PCstats.com Newsletter today!




No comments:
Post a Comment